Functional Encryption overcomes all-or-nothing limitation of traditional public key encryption. However, there are still very few works that combine access control and function evaluation with concrete schemes. Access control helps maintain the confidentiality of sensitive data by limiting access to authorized personnel only, provides centralized control over access permissions and reduces administrative overhead.

Credit: Haifeng QIAN, Cheng LIN, Qiaohan CHU, Jie CHEN
Functional Encryption overcomes all-or-nothing limitation of traditional public key encryption. However, there are still very few works that combine access control and function evaluation with concrete schemes. Access control helps maintain the confidentiality of sensitive data by limiting access to authorized personnel only, provides centralized control over access permissions and reduces administrative overhead.
To solve the problems, a research team led by Haifeng QIAN published their new research on 15 June 2024 in Frontiers of Computer Science co-published by Higher Education Press and Springer Nature.
The team proposed partially-hiding functional encryption schemes with fine-grained access control. Briefly speaking, ciphertexts are generated in accordance with an access policy and secret keys are associated to an attribute and also to being bound to a function. Decryption succeeds only when the attribute in the key satisfies the access policy in the ciphertext.
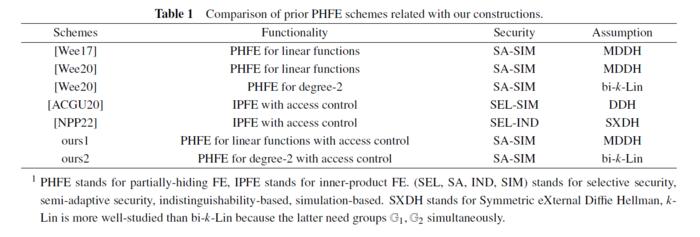
They follow the framework of Wee’s work (TCC’ 2020) and use the underlying inner product FE with access control (ASIACRYPT’ 2020) relying on the dual system encryption methodology. They give a clear solution to combine PHFE for linear functions with inner product FE with access contro. Then, use the the PHFE for linear functions with access control as a building block and leverage it to achieve PHFE for degree-2 polynomials with access control.
Their two constructions both achieve semi-adaptive, simulation-based security under standard assumptions. The security relies on the reduction from FE for quadratic functions to that for linear functions.
Future work can explore more general functional encryption with access control and apply into practical constructions.
DOI: 10.1007/s11704-023-3461-6
Journal
Frontiers of Computer Science
Method of Research
Experimental study
Subject of Research
Not applicable
Article Title
Partially-hiding functional encryption for degree-2 polynomials with fine-grained access control
Article Publication Date
15-Jun-2024