In a groundbreaking study that has caused a stir in the realms of cybersecurity and privacy, researchers from the University of Florida and the University of Electro-Communications in Japan have unveiled a substantial vulnerability in the design of digital microphones. This vulnerability stems from the radio frequency emissions produced by many modern microphones, which serve as an unintended channel for eavesdropping. Utilizing inexpensive equipment, anyone could potentially capture these radio signals, offering a real-world avenue for invasion of privacy and unauthorized surveillance.
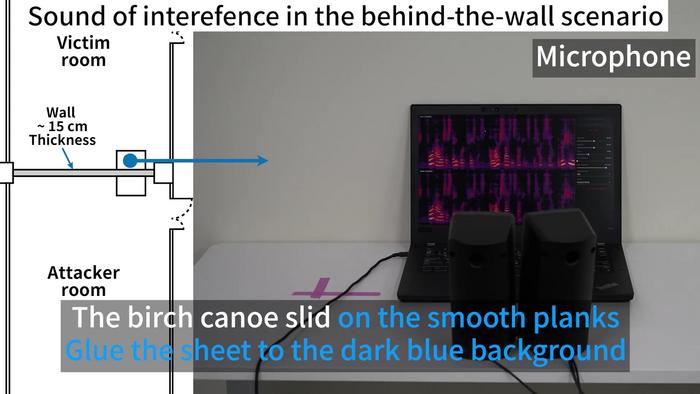
The study showcases a harrowing demonstration: a voice, distorted by static, comes through speakers conveying seemingly random yet distinctly recognizable phrases. For instance, the chilling phrase, “The birch canoe slid on the smooth planks,” emerges from the static, conjuring images of spectral messages transmitted through what the researchers have termed a “microphone attack.” This phenomenon is not derived from some supernatural source; instead, it highlights the invasive capabilities of radio signals emitted by everyday electronic devices like laptops and smart speakers.
The researchers utilized commercial-grade microphones for their experiments and discovered that these devices emit stray radio signals while processing audio. These emissions can inadvertently carry audible conversations, revealing a significant issue in the design and regulation of microphone technologies within consumer electronics. By leveraging simple radio receivers coupled with rudimentary antennas, they successfully intercepted these signals. Notably, the entire setup could cost around a hundred dollars, exemplifying the ease and accessibility of conducting such a breach.
The implications of this vulnerability could be far-reaching, sparking concerns not only within the private sector but also extending to national security. Eavesdropping via the methods outlined in this study does not require any direct access or tampering of the recorded devices. Once activated, the microphones in laptops and speaker systems can transmit audible conversations, exposing users to risks ranging from corporate espionage to invasive monitoring by governmental agencies. The prospect of private conversations being intercepted instills fear in the hearts of many, showcasing an urgent need for systemic improvements in microphone technology.
Experimental tests conducted during the study included a range of devices, from standard laptops to smart speakers like Google’s Home device. Particularly, laptops proved to be the most susceptible to eavesdropping efforts, primarily due to their design that incorporates long cables which function as antennas, amplifying the radio signals further. These findings underscore how embedded microphone technology needs a keen reevaluation to address these security concerns.
Furthermore, the research team employed advanced machine learning programs to analyze and transcribe the intercepted signals. Through sophisticated algorithms, they demonstrated the effectiveness of filtering out noise from the intercepted radio waves, elucidating spoken words in a coherent manner. This capability allows for the scanning of conversations for specific keywords or phrases, dramatically increasing the potential misuse of such technology in unethical ways.
The exciting revelation here is that the researchers have already proposed a range of modifications that manufacturers might implement to mitigate these risks. By altering the microphone placements within devices or refining audio processing techniques, manufacturers could substantially reduce the intelligibility of these unwanted radio emissions. These straightforward design tweaks could offer a sweeping improvement to the security posture of consumer electronics, protecting users from potential breaches while they go about their daily lives.
Nevertheless, the researchers have reached out to manufacturers to discuss these proposed changes, though the future remains uncertain concerning whether or not companies will heed their recommendations. The necessity for proactive measures cannot be overly emphasized, as the stakes involved rise with the increasing integration of technology in everyday life. Consumers deserve assurance that their devices respect their privacy, a fundamental principle warranting rigorous attention from both researchers and industry stakeholders alike.
As calls to action amplify, consumers and tech companies alike must engage in dialogue surrounding the ethical use of technology, emphasizing collective responsibility in ensuring privacy and security. There is ample incentive for manufacturers to heed this research, as market competition and consumer awareness rise. Failing to adapt could leave companies vulnerable to reputational damage in an era where consumer protection is paramount.
While the technology that permeates everyday lives brings unprecedented convenience and utility, these advancements can come at a perilous cost if adequate security measures are not prioritized. Addressing design vulnerabilities in digital microphones is just one of many steps that must be taken to preserve user privacy and ensure a safer digital environment for all. The desire for innovation must align with the ethical responsibility to safeguard information and privacy, creating an atmosphere in which consumers can benefit from technology without fear of exploitation.
The findings of the University of Florida and University of Electro-Communications’ study serve as a wake-up call in the digital age, emphasizing the need for ongoing research in the field of cybersecurity. With the rapid development of technology, especially in the context of artificial intelligence and machine learning, the landscape of threats to privacy continues to evolve, necessitating an equally dynamic response from researchers, developers, and policymakers alike.
In closing, as technology continues to intertwine itself more deeply into the fabric of daily life, it becomes increasingly crucial for both consumers and manufacturers to prioritize the design of secure systems and devices. This study highlights an unsettling reality of modern technology—1 that while it provides endless benefits, it simultaneously opens doors to vulnerabilities, requiring an unwavering commitment to protect against unauthorized access and exploitation of sensitive information.
Subject of Research:
Article Title: Sound of Interference: Electromagnetic Eavesdropping Attack on Digital Microphones Using Pulse Density Modulation
News Publication Date:
Web References:
References:
Image Credits: