The security of traditional attribute-based searchable encryption schemes relies on traditional number-theoretic assumptions, and thus they are not able to resist the threat of quantum algorithms. Meanwhile, existing lattice-based searchable encryption schemes have two main problems: one is the low efficiency of the execution of encryption, key generation and search algorithms. The second is the large space required for storing search trapdoors.

Credit: Yang YANG, Guoyin ZHANG, Sizhao LI, Zechao LIU
The security of traditional attribute-based searchable encryption schemes relies on traditional number-theoretic assumptions, and thus they are not able to resist the threat of quantum algorithms. Meanwhile, existing lattice-based searchable encryption schemes have two main problems: one is the low efficiency of the execution of encryption, key generation and search algorithms. The second is the large space required for storing search trapdoors.
To solve the problems, a research team led by Yang YANG published their new research on 15 June 2024 in Frontiers of Computer Science co-published by Higher Education Press and Springer Nature.
The team proposes an offline/online attribute-based searchable encryption scheme from ideal lattices (ABSEIL). Benefiting from the keyword search function of ABSEIL scheme, authorized consumers can efficiently retrieve the desired data with a lightweight search trapdoor. Through online/offline technology, complex arithmetic operations in encryption and key generation algorithms are pre-executed in the offline phase, and the online phase only involves a few arithmetic operations. Besides, ABSEIL scheme incorporates the proxy re-encryption mechanism for completing end-to-end data sharing.
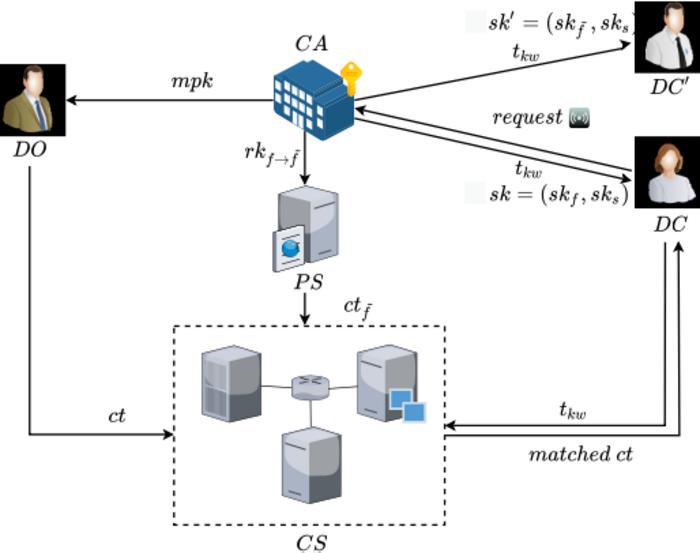
ABSEIL involves five types of participants: central authority (CA), data owner (DO), data consumer (DC), proxy server (PS) and cloud server (CS).
CA plays the role of initializing the system. Then it generates the master public key () for all entities together with the master secret key for itself. Also, it grants secret key to all data consumers (See ① and ②). DO encrypts data, and uploads the ciphertext to CS (See ③). Before decrypting , DC requests a searchable trapdoor from CA and forwards it to CS to search for matched . Moreover, DC can initiate a request to CA to produce a re-encryption key . Then CA transfers to PS. In this setting, DC delegates the decryption right to the through the authorization of CA (See ④ and ⑤). PS utilizes to produce a fresh re-encrypted ciphertext , then transfers to CS (See ⑥). CS supplies storage services. Furthermore, CS utilizes to search for matched ciphertext for DC (See ⑦).
DOI: 10.1007/s11704-023-3128-3
Journal
Frontiers of Computer Science
Method of Research
Experimental study
Subject of Research
Not applicable
Article Title
Offline/online attribute-based searchable encryption scheme from ideal lattices for IoT
Article Publication Date
15-Jun-2024